The beginning of the next Industrial Revolution began on August 6th, 1991, when the World Wide Web became a global interconnected computer network available to the masses. We’ve come to rely on the ability to have instant access to our email and social media, not to mention the answer to almost any question at our fingertips with a quick Google search. There is so much that the internet can offer people nowadays, and now with centurylink internet plans as well as many others available, people are able to use the internet for what they need.
Today, we’re taking that a step further. We have the ability to do such things as adjust our thermostat from the other side of the world, look through our refrigerator door to look for a snack or have it order milk when we’ve run out, receive text alerts that it’s time to swap the laundry, or even – my personal favorite – ask Alexa to play our favorite song.
Tomorrow, we’ll be able to detect breast cancer sooner with “smart bras”, reduce traffic and smog in heavily populated cities using sensors and relax (while still being aware of our surroundings) on that cross-country road trip in our autonomous cars.
Autonomous vehicles have become a concept of today with the growing production and demand for self-driving cars and trucks. You can learn about the technological advancement of the automobile industry through https://torc.ai/trucking/ or similar websites.
However, these new technological advancements in our world have some drawbacks, including potential issues concerning cyber safety.You automatically inherit some risk of cybercrime if you – or your kids – are using a device connected to the Internet. As the number of connected devices increase, the amount and type of data that is collected will be exponential and the statistics behind the Internet of Things (IoT) are incredible:
- There were already more devices connected to the Internet than there were people on Earth as early as 2008.
- In 2018, the number of IoT-connected devices surpassed mobile devices.
- It’s predicted that there will be more than 50 billion devices connected to the Internet by 2020.
- This means there will be over three IoT devices for every human on planet earth.
- Cisco predicts that 250 devices will connect to the Internet every second by the year 2020.
“Thinganomics 101”
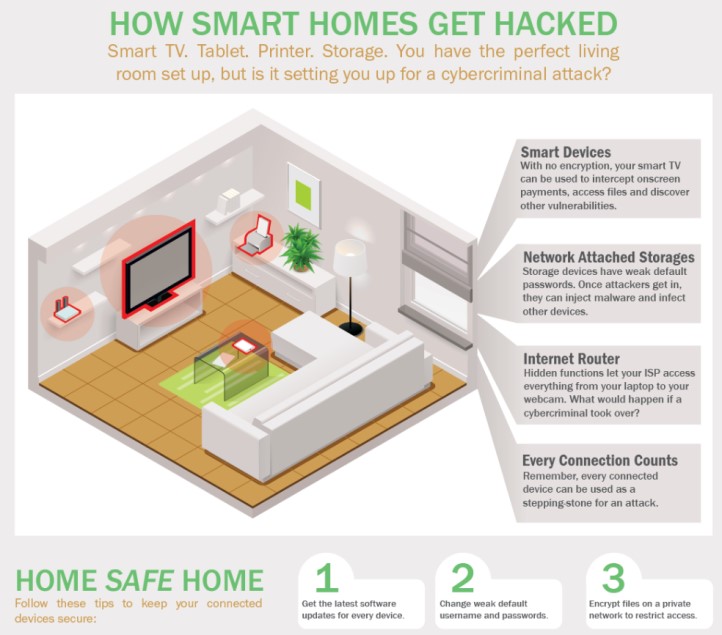
Devices such as smart TVs, Fitbits, computer/security cameras, tablets, printers, video games, speakers, personal assistants, and so on need to access the Internet to work. Once a device is connected to the Internet, it’s assigned an IP address; for comparison, it’s similar to a mailing address. The key to this digital home is a user name and password. Most devices are issued with easily traceable credentials that, with just a little work, you can find with a quick Google search. Once a hacker has gained access to a device, they have the ability to search for any other venerable devices on ANY network you connect through, using a virus referred to as a “BotNet.” Below are some recent examples of what this type of attack can do.
- In March 2019, hackers shutdown the ENTIRE computer system of Lynn Public schools, which is the 3rd largest school district in MA with an enrollment number of 15,200 students. Can you imagine being without access to your work information for multiple days while still having to work?
- Baby monitors have come a long way and now offer the ability to see your little bundle of joy, live, from anywhere in the world on your phone or tablet. The newest systems also offer the ability to alert you when there’s movement within the cameras scope of view.
- When hackers gain access to cameras they can see view the camera in real time, as well as access features such as being able to change the view or even being able to speak through it.
- Automotive cyber-security experts Charlie Miller and Chris Valasek tested the security features of a Jeep and successfully hacked the car’s GPS system.
- After hacking the GPS system, they were able to access the car’s computer system and were able to remotely turn the wheel, activate the parking brake and successfully take control of the car to crash it into a ditch.
How to Protect Yourself
Many companies are starting to offer cyber insurance policies, but regardless of whether or not you invest in additional cyber coverage, you should proactively protect yourself. Below are some common tips from the biggest Internet security companies like Kaspersky and Symantec that if you aren’t already doing, you should implement as soon as possible.
- Always change default passwords, replacing them with strict and complex ones and be sure to update them regularly.
- Always install patches and updated firmware, even if it’s necessary to do so manually.
- Use one network for connected appliances and gadgets, and a separate network for your computers, tablets and phones. This way, if someone hacks your device network, they won’t be able to access your accounts with personal information.
- Secure the property’s wireless network and cloud-enabled devices with a firewall.
- Use a regularly updated anti-virus program across all computers and make sure all computers and networking equipment are patched regularly.
Please contact us if you would like to review your available options.
